BLOCK OUTDATED OPERATING SYSTEMS WITH MICROSOFT DEFENDER FOR CLOUD APPS (CLOUD APP SECURITY)
INTRODUCTION.. In this write up I will be configuring Microsoft Defender for Cloud Apps (old name is Cloud App Security) and Conditional Access to block outdated operating systems from accessing Microsoft 365 services within my tenant.
LICENSING
First thing you want to figure out, is licensing. You must have a license that enables “Microsoft Defender for Cloud Apps Discovery” and not “Microsoft Defender for Cloud Apps.” At the time of writing EM+S E5 sku will not work but Microsoft 365 E5 Security sku will. You will also need Azure Active Directory Premium P2 license.
SETTING UP CONDITIONAL ACCESS
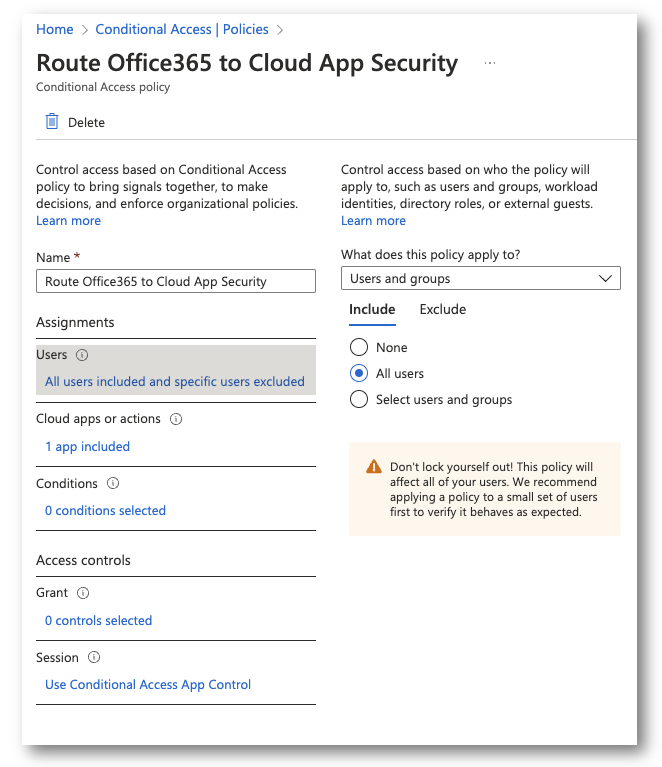
Once we have the proper licensing we need to route applications to Microsoft Defender for Cloud Apps. In the Azure Portal, go to Conditional Access and create a new Policy.
ASSIGNMENTS
In my assignments, I selected all users and excluded my break-glass account.
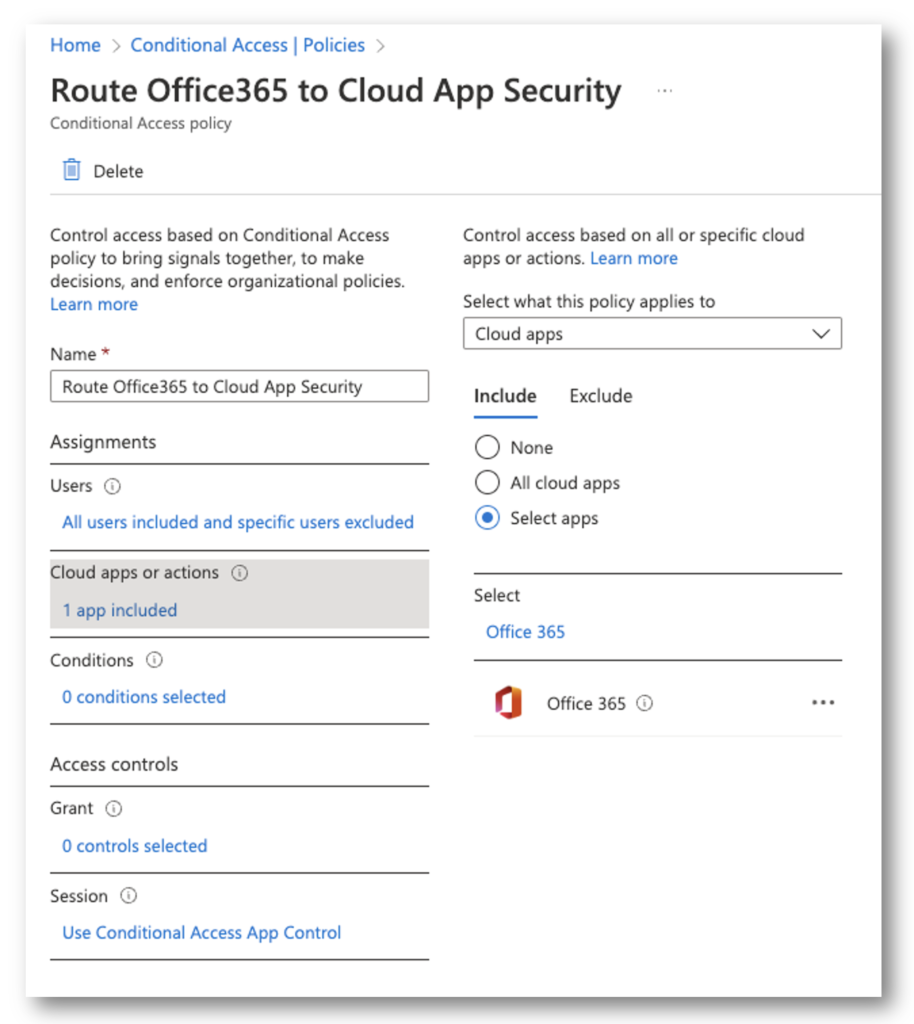
CLOUD APPS OR ACTIONS
Next, I selected the Office 365 application. You can configure All Cloud Apps or whichever application you prefer. Office 365 will not only encompass the applications, but the web portals as well (login.microsoftonline.com)
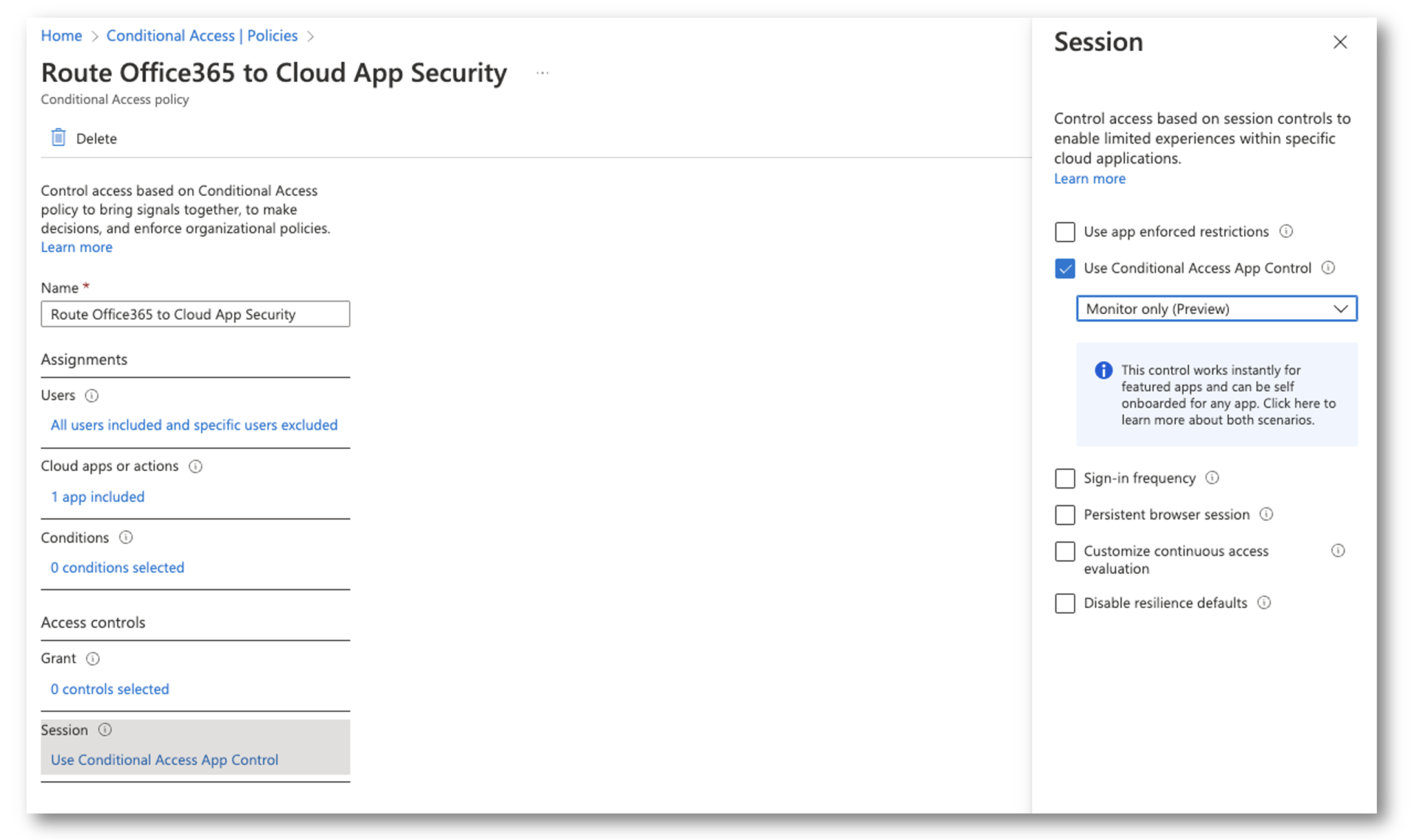
SESSION CONTROL
Under “Session”, select Use Conditional Access App Control and select Monitor Only.
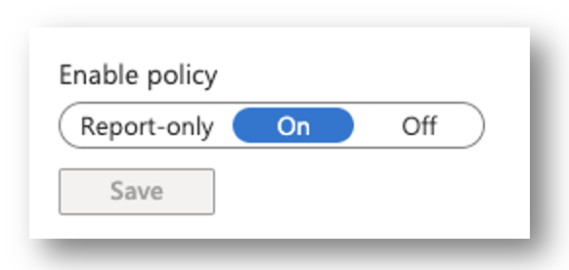
ENABLE POLICY
Finally, enable the policy and save. It will not work if you have it configured in Report-Only mode!
SETTING UP DEFENDER FOR CLOUD APPS and CONNECT OFFICE 365
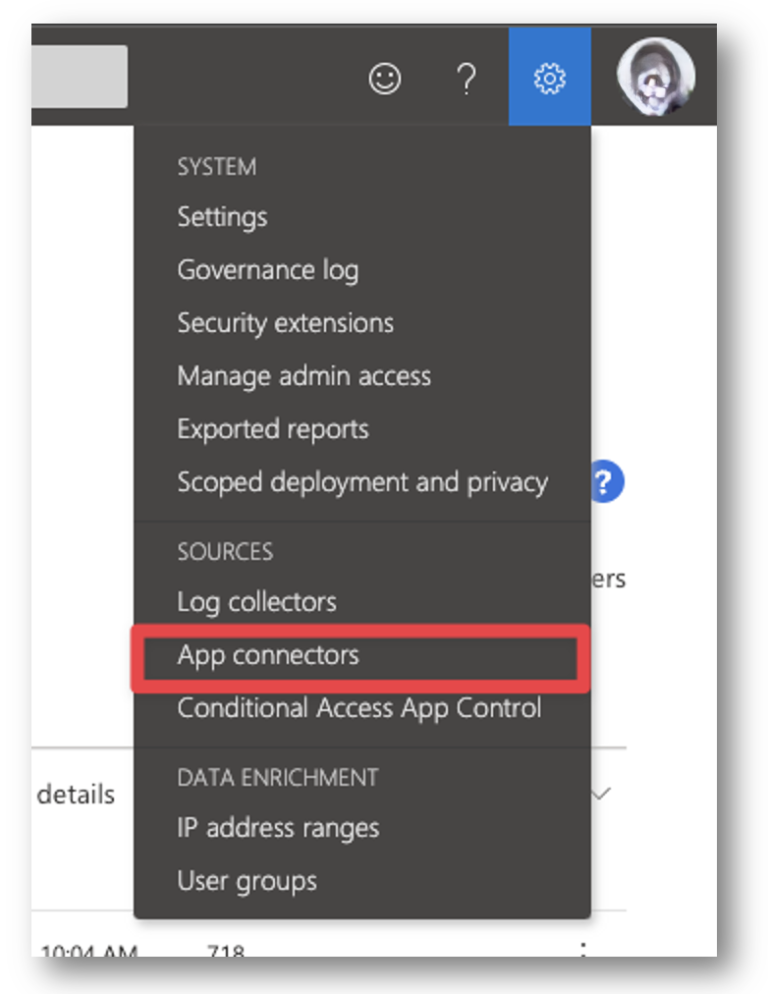
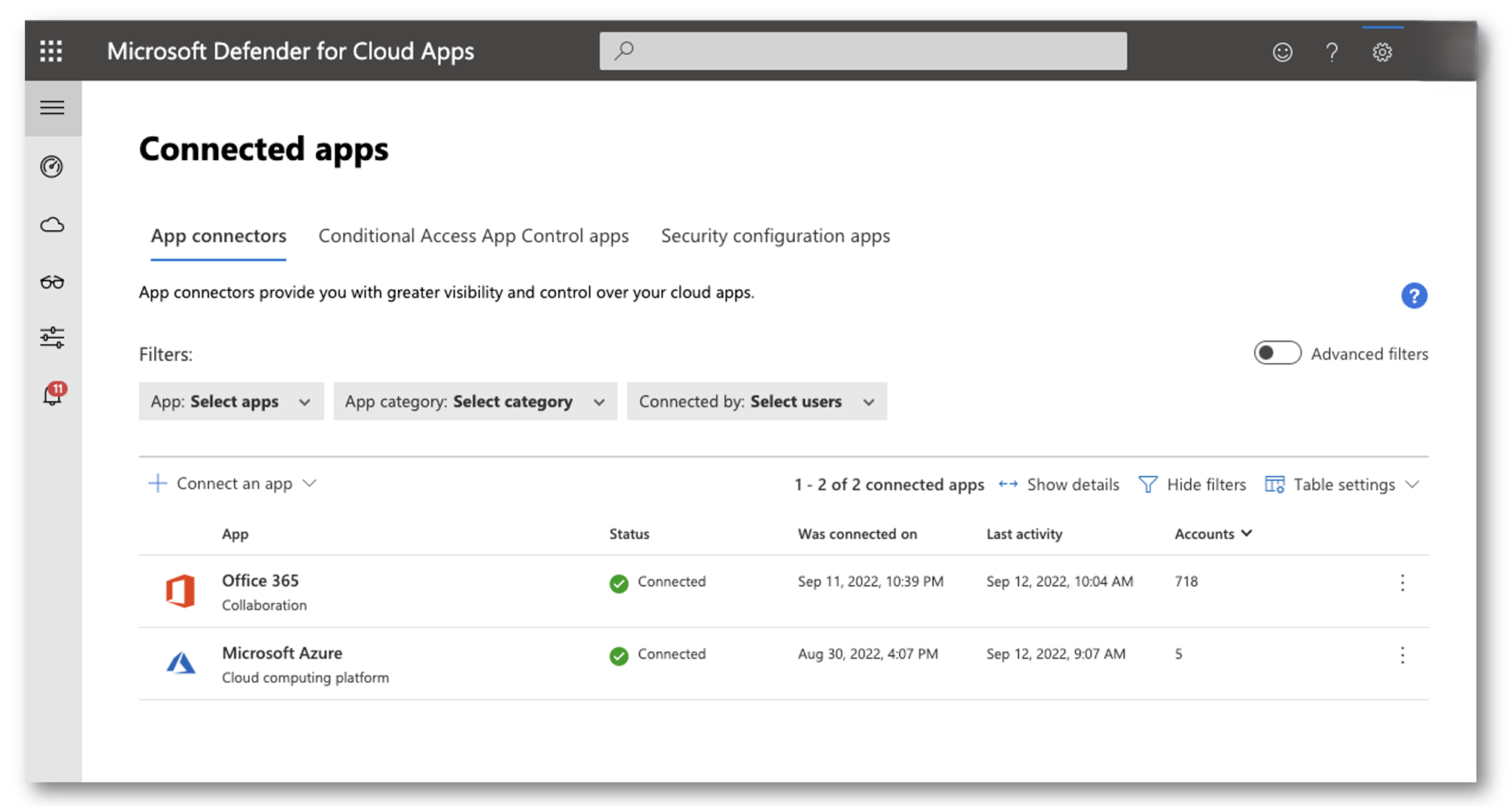
First, we must connect Office 365 with Defender for Cloud Apps. In the top right corner, click the settings cog and select App Connectors.
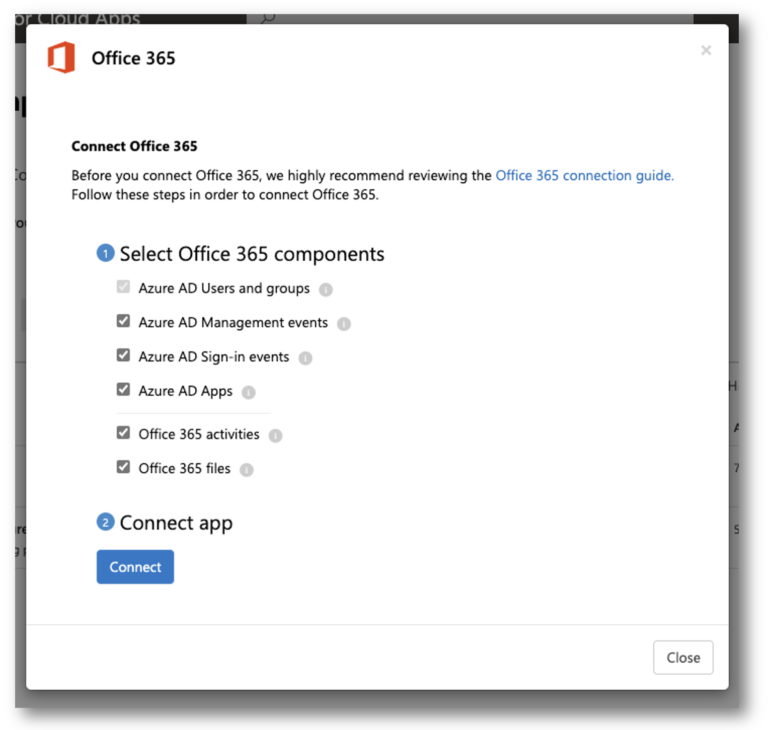
Next, Select Connect an App and select Office 365. You will need an Office 365 Global Admin to connect the application to Defender for Cloud Apps.
Finally, you will see it connected. I recommend giving it 15-30min to parse all the logs depending on how large your organization is.
CONDITIONAL ACCESS APP CONTROL APPS
Next, head over to the Defender for Cloud Apps Portal. In the top right corner, click the settings cog and select Conditional Access App Control.
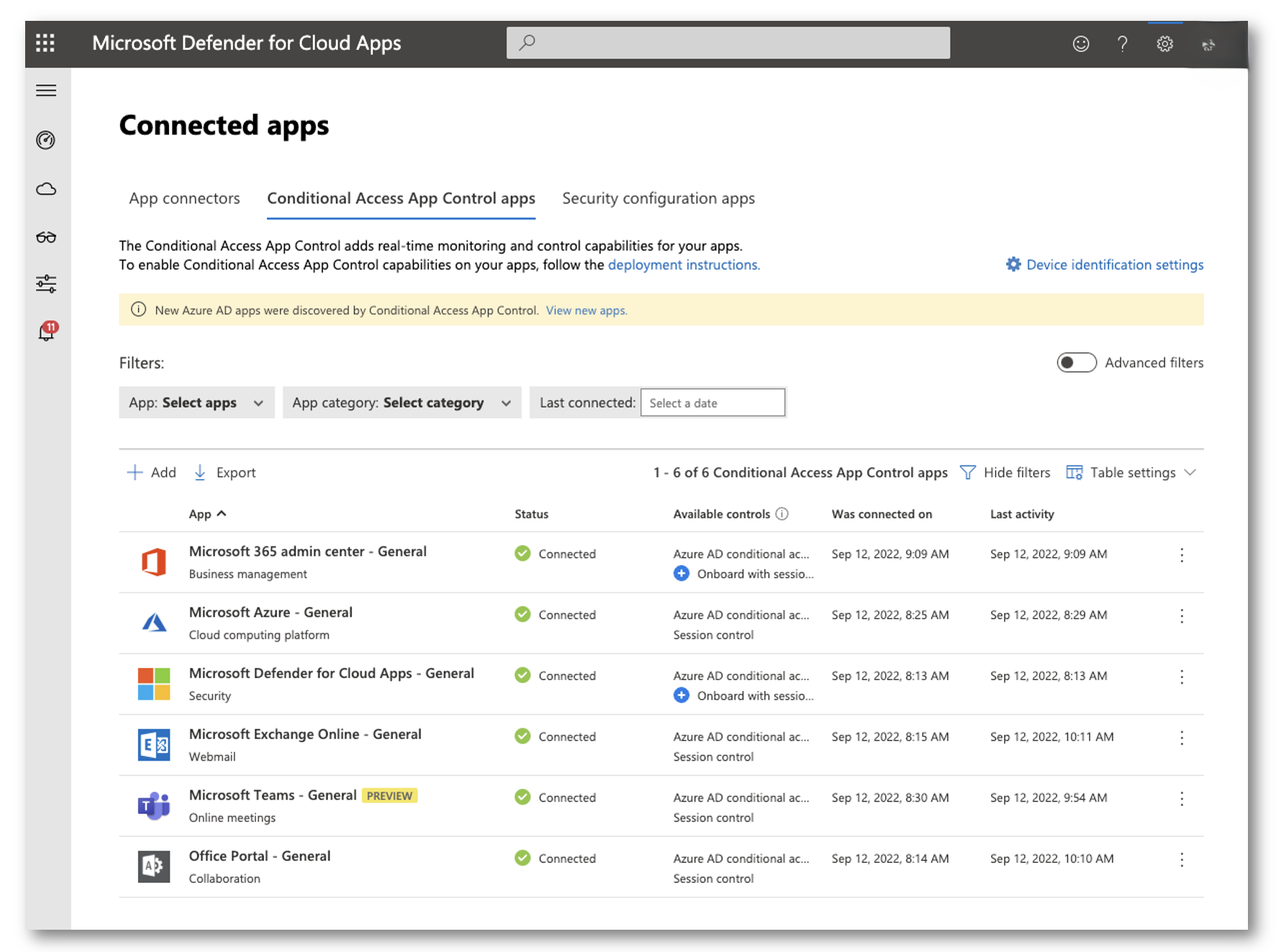
If you do not see any applications listed in the Conditional Access App Control Apps screen, you may have to wait a bit. As users sign into applications and get caught through the Conditional Access Policy applications will begin to appear in this portal. You can also try to jump-start it by launching a in-cognito window and signing into some Office 365 web apps using an account that you are not sign into, and that will be caught via the conditional access policy.
CONFIGURE CONDITIONAL ACCESS APP CONTROL
Next, expand the left ‘hamburger’ menu and go to Control > Policies > Conditional Access
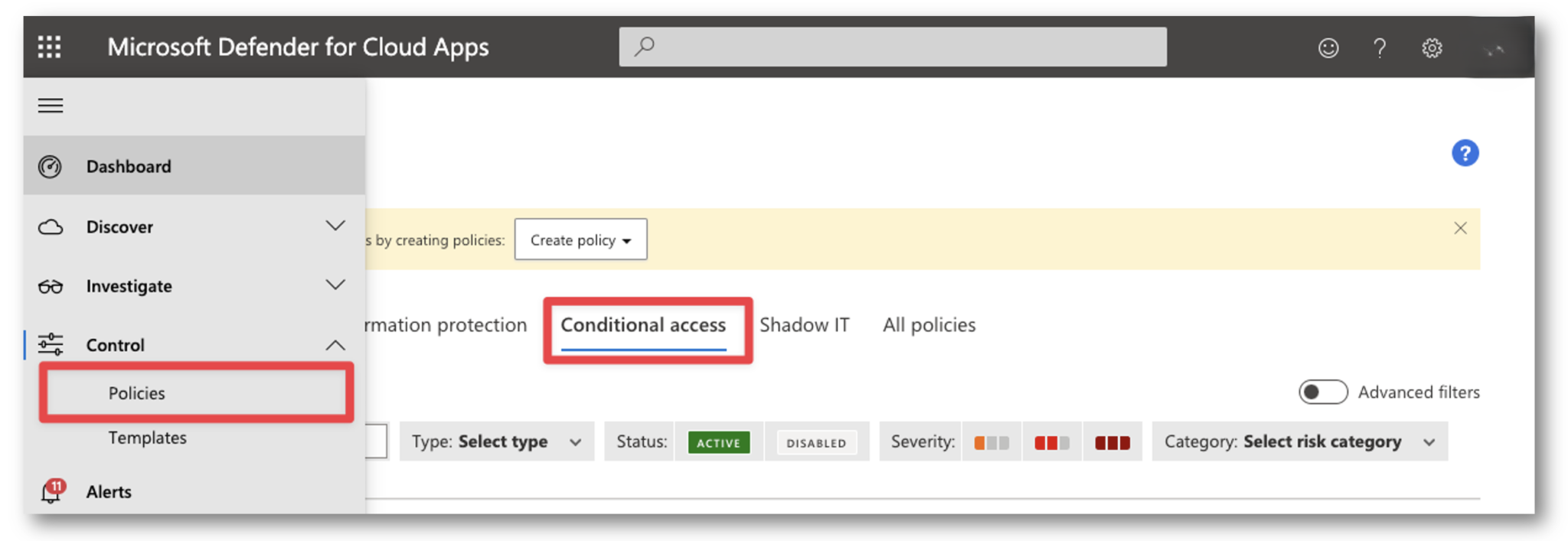
Click + Create Policy > Access Policy
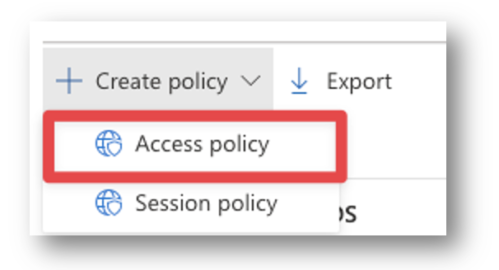
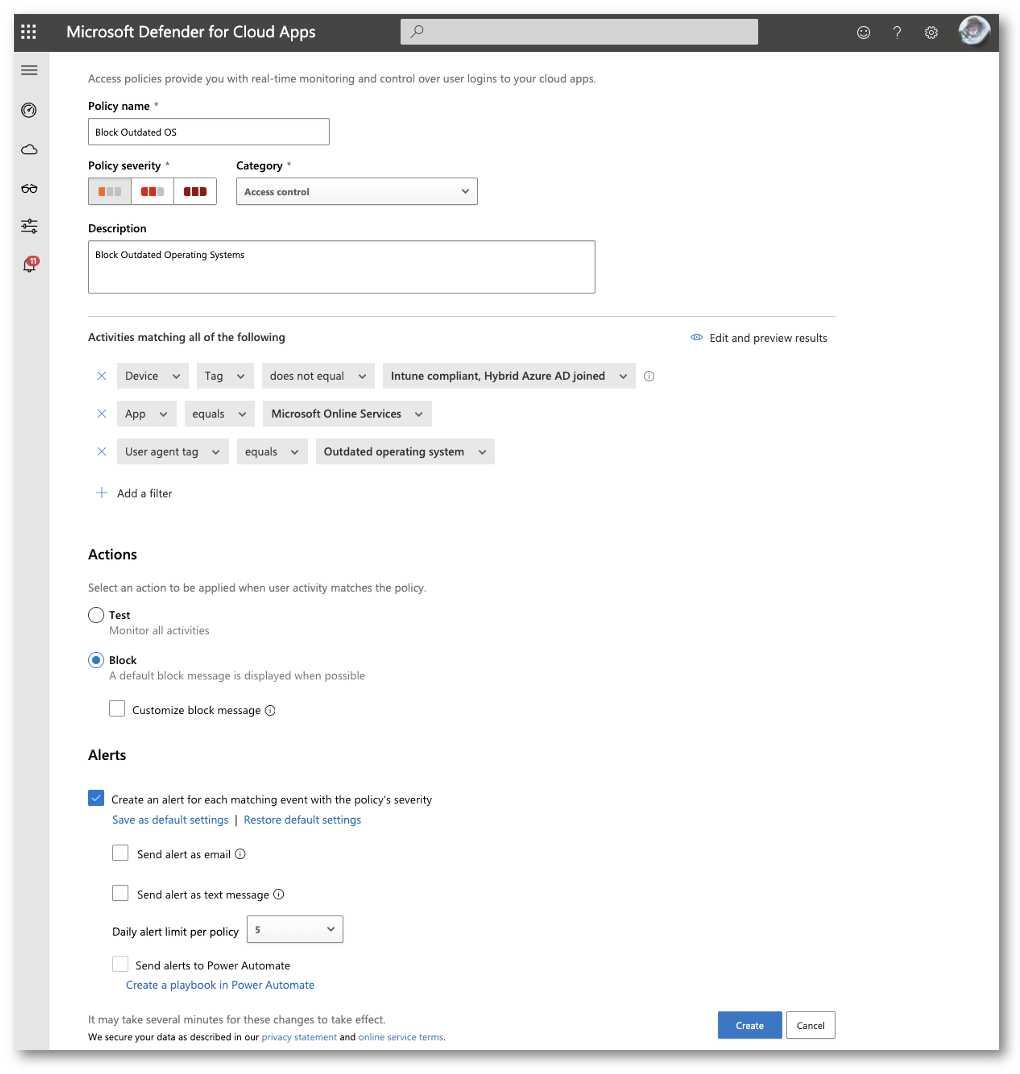
Give your policy a proper name and then under the “Activities matching all of the following” select which apps this policy will apply to. I want to block all Microsoft Online Services so I will select “Microsoft Online Services” but you can get more granular and block only Exchange Online for Example.
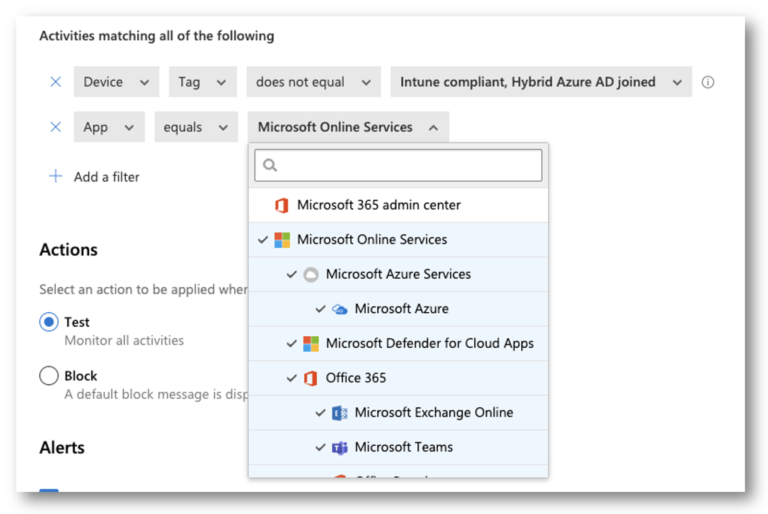
Add another filter and make it the following
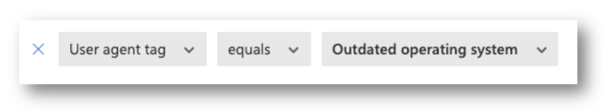
NOTE: Outdated Operating System filter in the User Agent tag is configured to be two major versions back.

Under Actions select “Block.” You can also configure a custom block message as well.
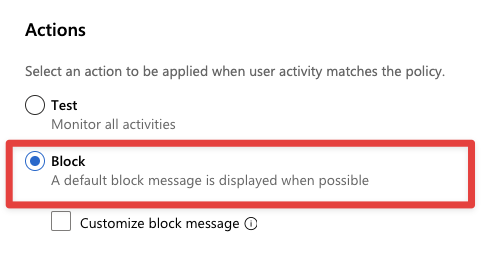
When you are all finished, select Create
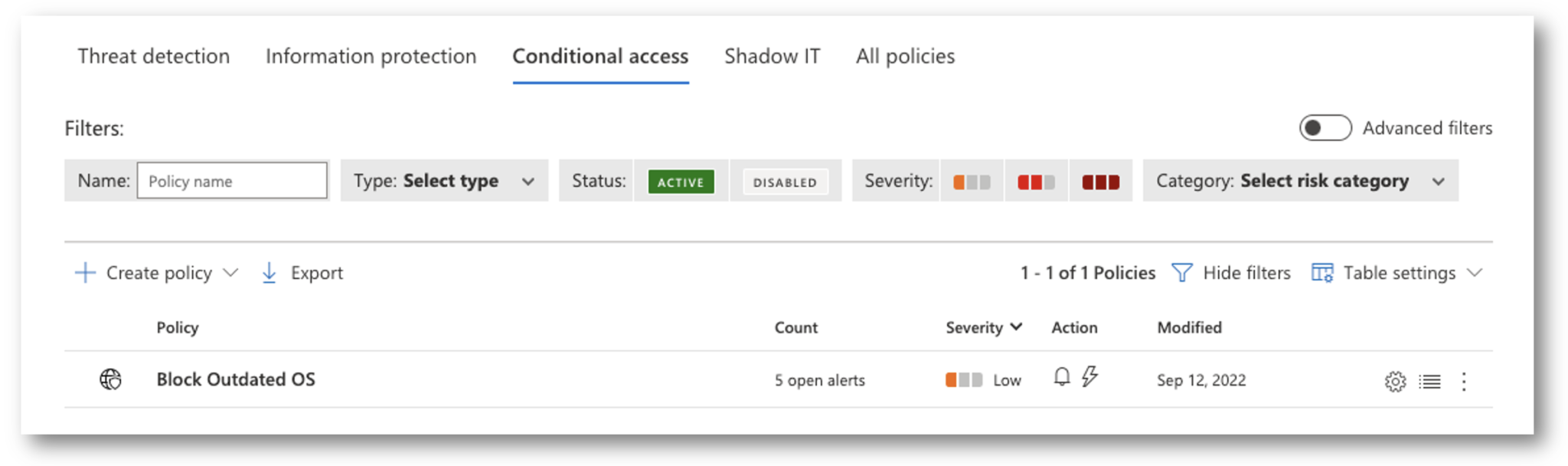
You will now see your newly created Conditional Access App Policy
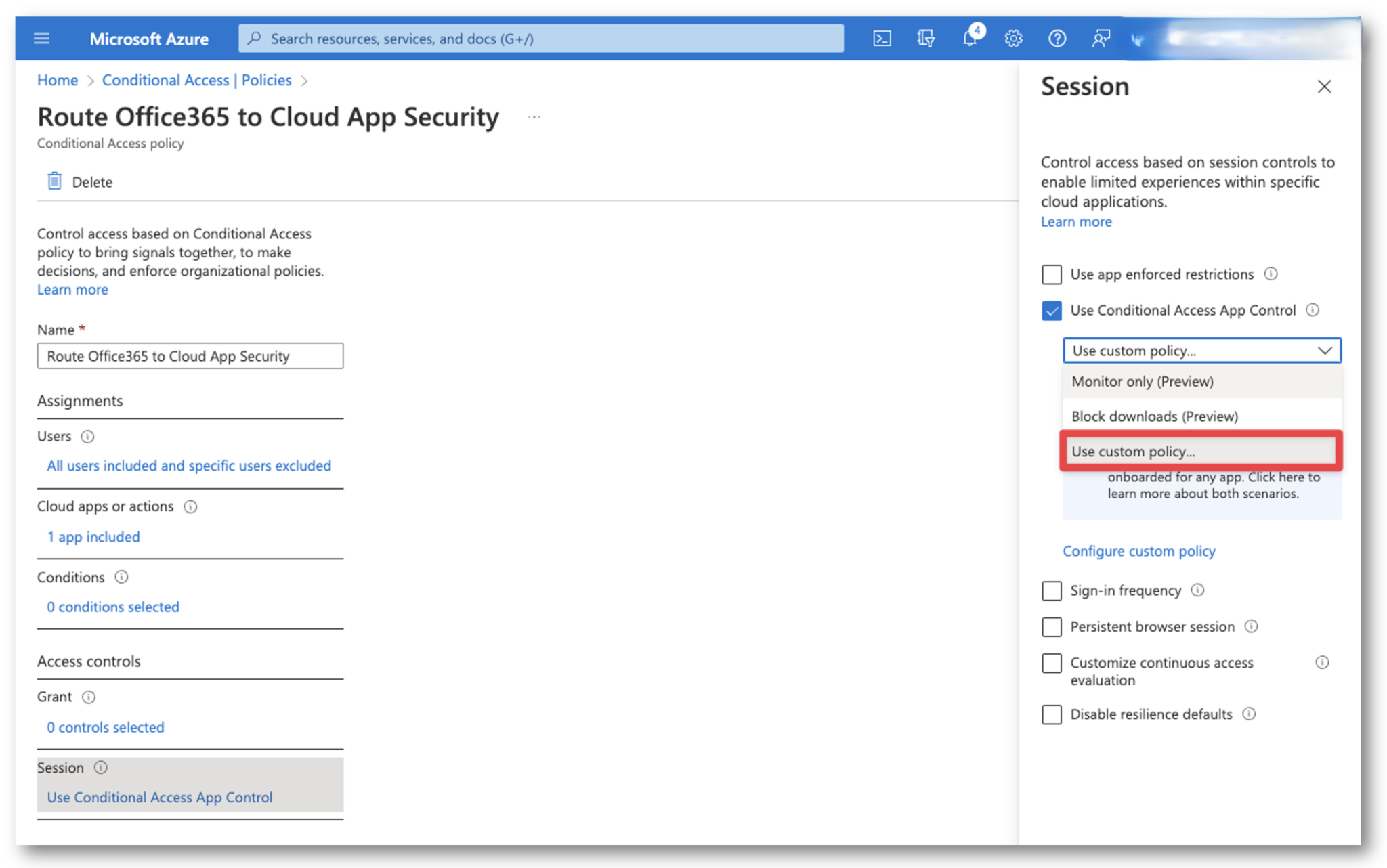
APPLY ACCESS POLICY TO AZURE AD CONDITIONAL ACCESS
Now we must go back and re-configure out Azure Active Directory Conditional Access Policy to use our new Defender for Cloud Apps Access Policy. Go to the Azure Portal > Conditional Access and edit the policy you created earlier. Under Session select Use Custom Policy… and then save your changes.
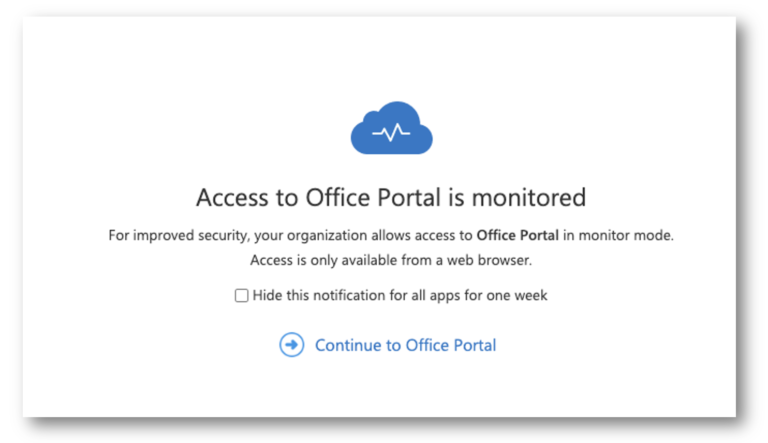
DISABLE REDIRECTION MONITORED MESSAGES
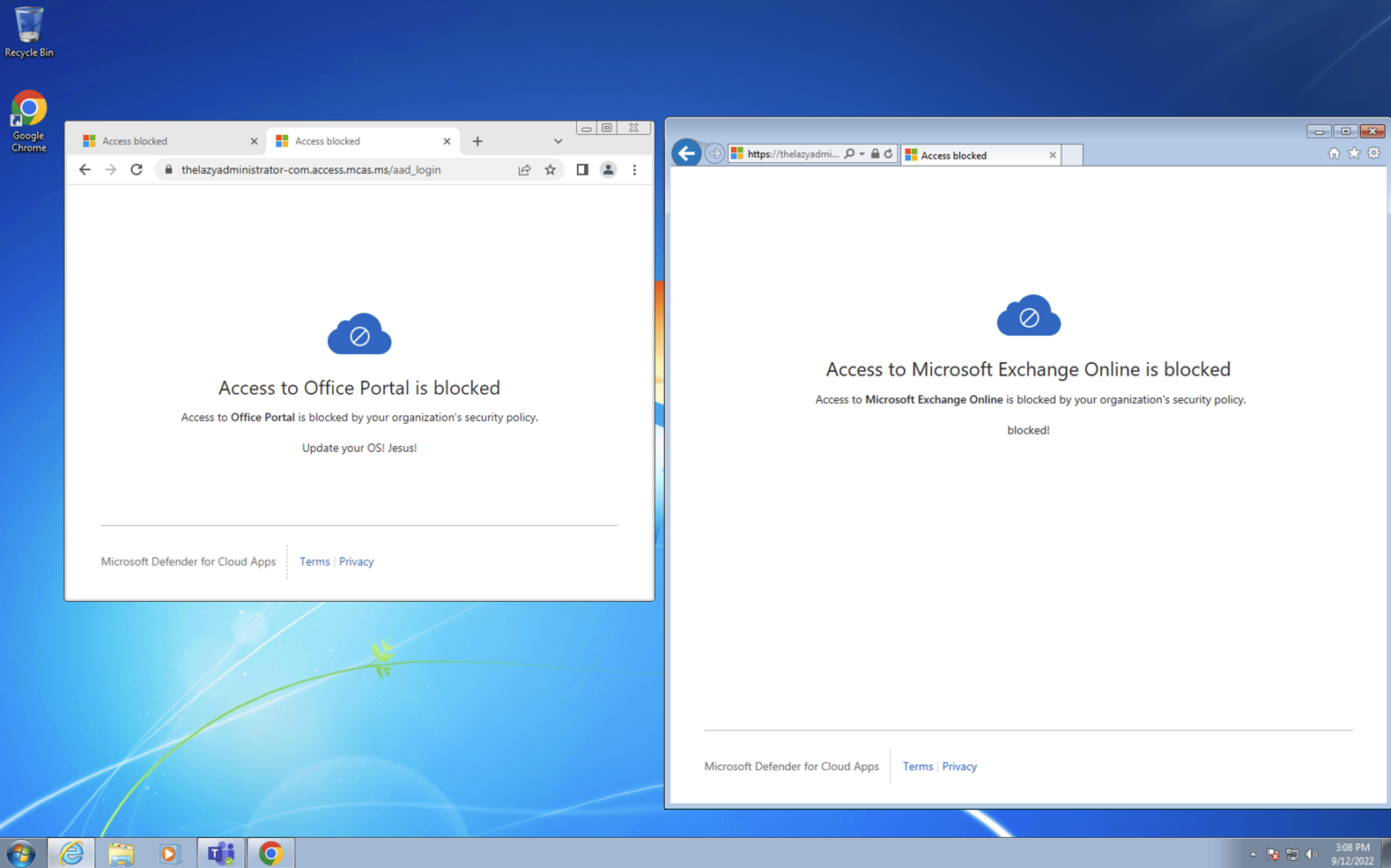
Lastly, users will see a monitoring message (seen below) when their applications are being monitored by Defender for Cloud Apps. This does not mean that they are being blocked but can cause confusion within an organization. It is for this reason that I disable the monitoring message so only users that are blocked will see a message.
In the top right corner of the Defender for Cloud Apps portal, select the Settings cog and then select Settings
In the menu under Conditional Access App Control select User Monitoring
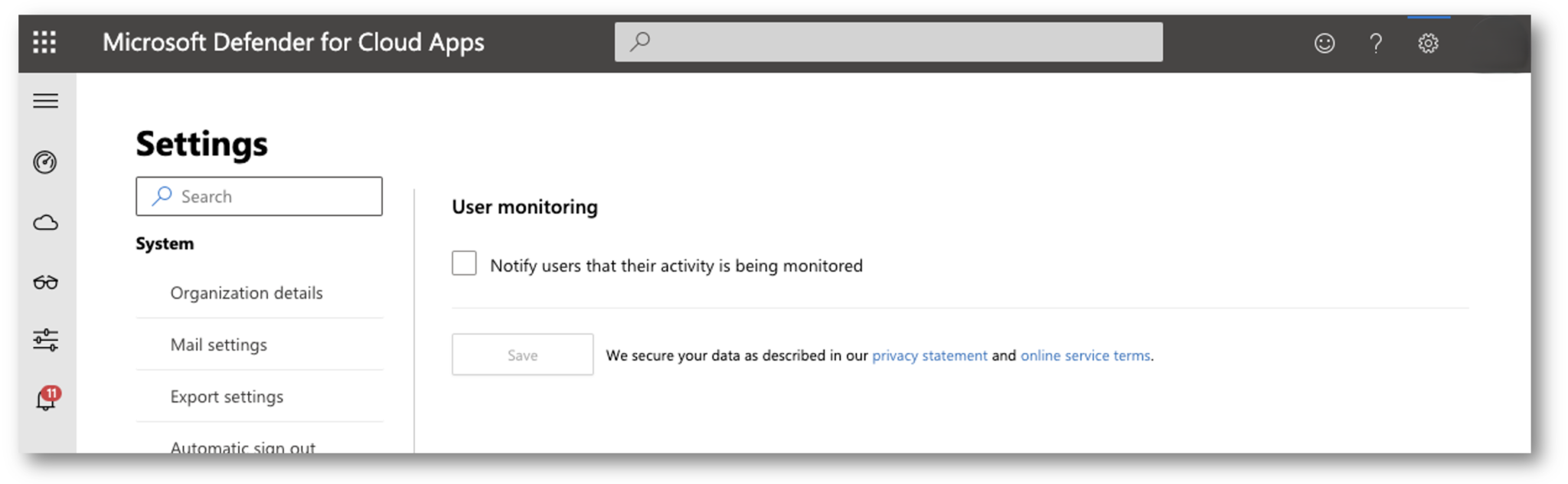
Uncheck “Notify users that their activity is being monitored.” and then click Save.
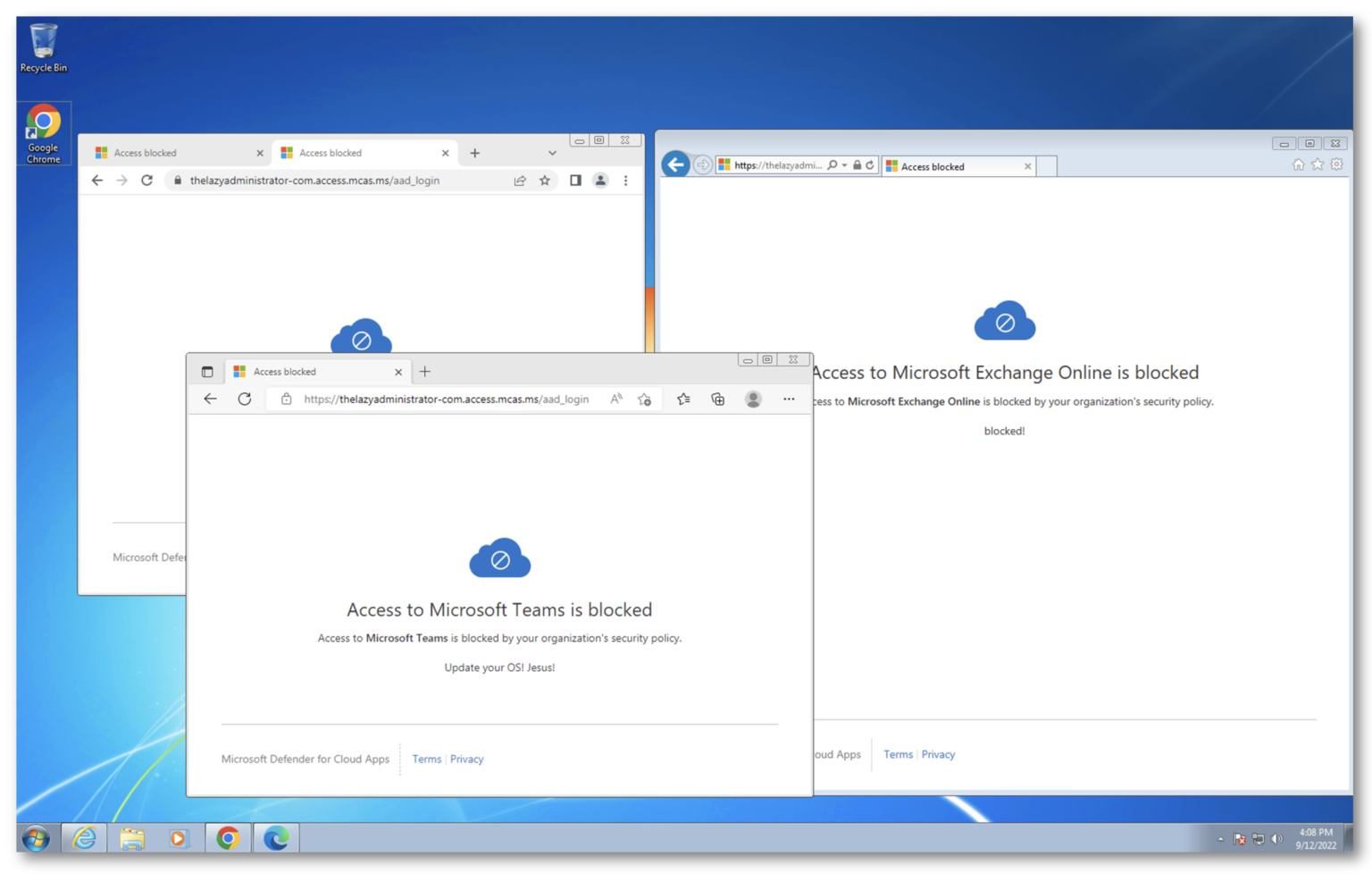
Done! Now when a user attempts to access Microsoft 365 services from a workstation with an outdated operating system they will be blocked.
Contact
Etecnest as your trusted IT and Cloud Service Provider. We are dedicated to delivering innovative solutions that propel your business into the digital future. Whether you are seeking robust IT services, comprehensive cloud solutions, or a tailored combination of both, we are here to meet your unique needs.
Our Address
J P Nagar 509 Area Pune 411032
Email Us
info@etecnest.com
Call Us
+91 7875092767